What is DevSecOps?
DevSecOps integrates security into every stage of your development pipeline, ensuring that security is not an afterthought but a continuous, automated process. It fosters a culture of Security as Code and Continuous Security, making your software development lifecycle (SDLC) more resilient and efficient.
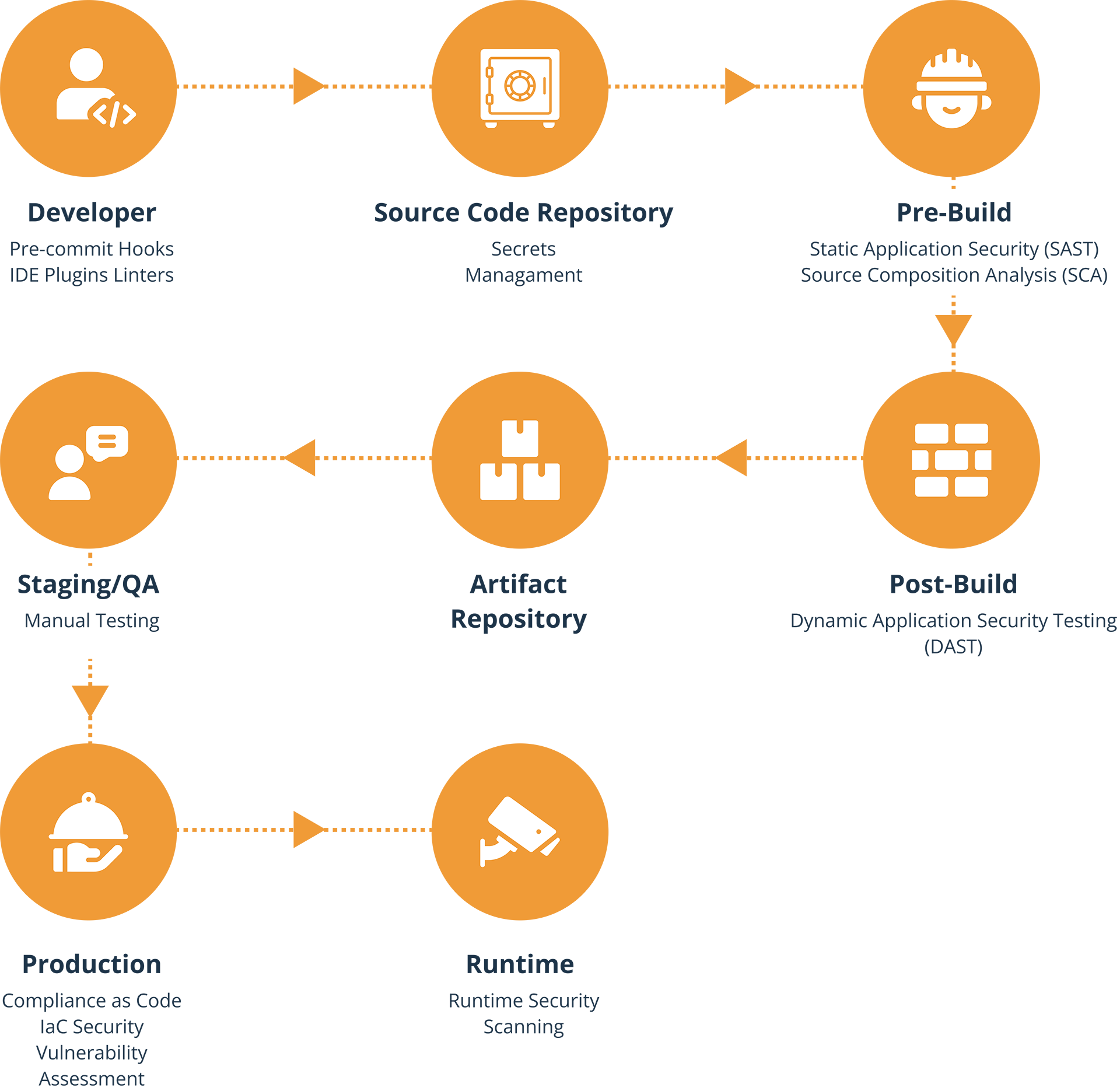
A Sample DevSecOps Pipeline
Here’s an example of a comprehensive DevSecOps pipeline
- Code Commit: Pre-commit hooks and IDE plugins enforce secure code practices.
- Build: SAST and SCA ensure early detection of vulnerabilities.
- Test: DAST analyses running applications, and container security reviews are performed.
- Deploy: Infrastructure security and compliance checks are conducted.
- Monitor: Continuous monitoring of security in production.
Key Benefits of Adopting DevSecOps
Faster Vulnerability Detection
By integrating security throughout the development pipeline, DevSecOps enables teams to identify and resolve vulnerabilities earlier, reducing the risk of security breaches.
Reduced Development Costs
Addressing security issues early in the software lifecycle helps avoid costly fixes in later stages, leading to more efficient development and significant cost savings.
Enhanced Software Reliability and Security
Continuous security checks ensure that your software is more robust and less prone to vulnerabilities, improving both reliability and trustworthiness in production environments.
Proactive Security
Traditional security testing often finds vulnerabilities late in the cycle, increasing costs and delays. By adopting a "Start Left" mentality, security is integrated early, leveraging Security as Code principles and automation.
Why Shift Left Isn’t Enough
Even shifting security earlier in the cycle may not fully prevent issues. If vulnerabilities are found during later stages, such as QA or production, mitigation becomes resource-intensive.

Start Left with Full Pipeline Security
To truly enhance security, you must enforce security at every stage of the development process:
- Developer: Use pre-commit hooks and linters for secure code.
- Source Code Repository: Secure secrets management and version control.
- Build and CI/CD: Automate Static Application Security Testing (SAST) and Software Composition Analysis (SCA).
- Staging/QA: Conduct manual and dynamic security testing.
- Production and Monitoring: Use runtime security scanning and continuous monitoring.
By embedding security from the start, you can prevent vulnerabilities before they grow, ensuring a more secure and resilient development lifecycle.
DevSecOps Tools & Practices Used
- Pre-Commit Hooks
- Static Application Security Testing (SAST)
- Software Composition Analysis (SCA)
- Artifact and Repository Scanning
- Infrastructure-as-Code Security
- Vulnerability Assessment
- IDE Security Plugins
- Dynamic Application Security Testing (DAST)
- Dockerfile Best Practices and Image Security
- Container and Kubernetes Configuration Security
- Compliance-as-Code
- Container Runtime Security


.jpeg)