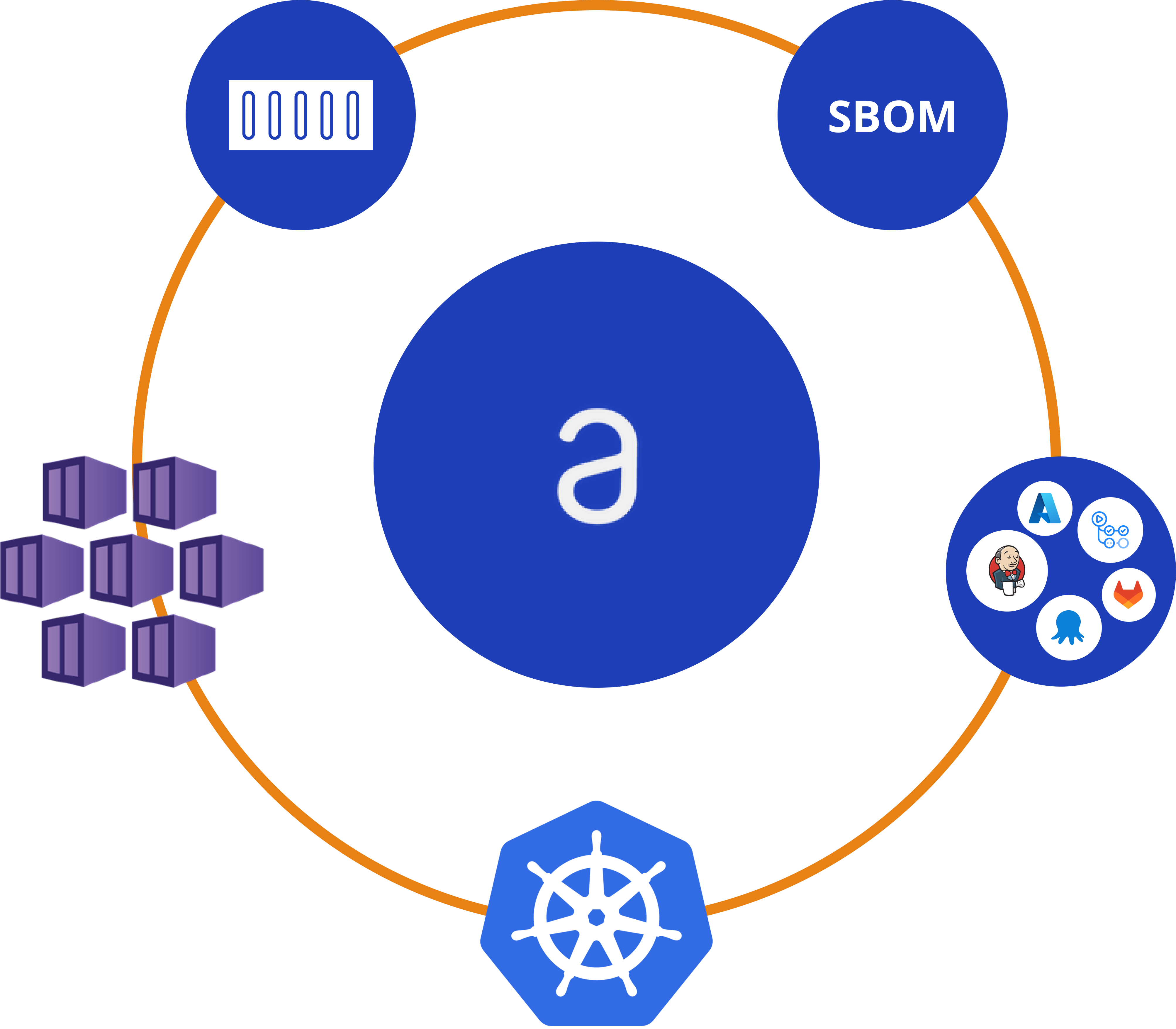
Why Anchore?
Anchore specialises in SBOM (Software Bill of Materials)-powered security, providing organisations with deep visibility into their software components. By automating security checks throughout the DevOps process, Anchore ensures a seamless developer experience while optimising velocity. Key capabilities include:
- End-to-End SBOM Management: Maintain an accurate inventory of software components to identify vulnerabilities and manage risks effectively.
- Vulnerability Scanning & False Positive Management: Detect and address vulnerabilities in container images, reducing the risk of security breaches.
- Flexible Policies for Compliance: Enforce security policies that align with industry standards and regulatory requirements.
- Continuous Visibility & Monitoring: Gain real-time insights into your software supply chain to proactively address potential threats.
Anchore's Key Capabilities
SBOM Drift Detection
Identify unauthorised changes in your Software Bill of Materials (SBOM) to ensure software integrity and prevent supply chain attacks.
Automated Vulnerability Scanning
Continuously scan container images and open-source components for known vulnerabilities, minimizing security risks.
Policy-Based Compliance Enforcement
Define and enforce security policies aligned with industry standards like NIST 800-53, CIS Benchmarks, and FedRAMP.
Real-Time Notifications & Alerts
Receive immediate alerts on security issues, misconfigurations, and compliance violations for proactive remediation.
Security Reports & Audit Trails
Generate detailed security reports and maintain audit logs to meet regulatory and compliance requirements.
Open Source Dependency Tracking
Monitor direct and transitive dependencies in your software to detect vulnerabilities and manage risks effectively.
Application-Level Risk Insights
Gain visibility into security risks at an application level, enabling targeted remediation and better decision-making.
Remediation Recommendations
Receive actionable insights and suggested fixes to quickly address security gaps and harden your software environments.
Anchore Use Cases
Anchore's solutions cater to various aspects of software security:
- CI/CD Pipeline Security and Compliance: Integrate security checks into your continuous integration and delivery pipelines to detect issues early.
- Kubernetes Image Scanning & Security: Ensure container images deployed in Kubernetes environments are secure and compliant.
- Container Security: Protect containerised applications from vulnerabilities and misconfigurations.
- Container Vulnerability Scanning: Identify and remediate vulnerabilities in container images before deployment.
- Container Registry Scanning: Automate the scanning of images in container registries to maintain security standards.
- DevSecOps: Embed security into your DevOps practices to build a robust DevSecOps culture.
- FedRAMP Vulnerability Scanning: Meet federal compliance requirements with specialised scanning capabilities.
- Federal Compliance: Ensure adherence to federal regulations and standards with comprehensive compliance features.
Addressing Common Security Challenges
Organisations often face challenges in maintaining compliance and managing vulnerabilities. Anchore assists in satisfying NIST 800-53 controls, including:
Vulnerability Scanning
(RA-5)
Automate the detection of vulnerabilities in software components to reduce security risks and maintain compliance.
Flaw Remediation
(SI-2)
Implement structured processes to quickly address security flaws and prevent potential exploits in your software supply chain.
Continuous Monitoring
(CA-7)
Maintain real-time visibility into security threats to detect, respond to, and mitigate risks before they escalate.
VIPERR Framework
Apply a structured approach with Visibility, Inspection, Policy Enforcement, Remediation, and Reporting to strengthen software security.
Why Choose Bion as Your Security Partner?
As an AWS Advanced Partner with deep expertise in DevSecOps and cloud security, Bion is uniquely positioned to integrate Anchore's solutions into your environment. Our services include:
- Consultation and Planning: Assess your current security posture and develop a tailored strategy for improvement.
- Implementation and Integration: Seamlessly incorporate Anchore's tools into your existing workflows and systems.
- Training and Support: Equip your teams with the knowledge and resources needed to effectively utilise Anchore's capabilities.
- Continuous Improvement: Provide ongoing support to adapt to evolving security landscapes and organisational needs.
Enhance your security posture, ensure compliance, and gain comprehensive visibility into your software supply chain with Bion and Anchore. Contact us today to schedule a consultation and take the first step toward a more secure future.



